What is API Discovery, and How to Use it to Reduce Your Attack Surface
Let's explore six practical methods and best practices for employing API discovery to safeguard your digital assets.
1. Use API Discovery Tools
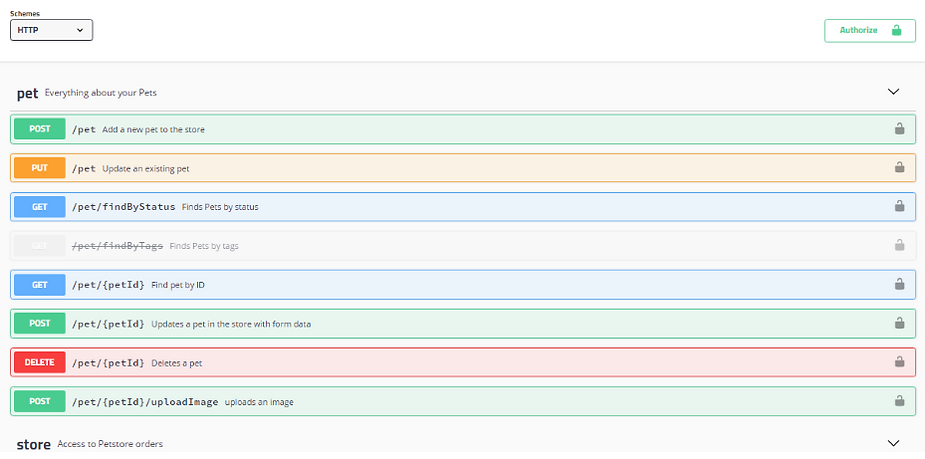
Automated API discovery tools are essential in identifying both known and unknown APIs. These tools scan various segments of your network and catalog APIs, offering insights into their operations and potential vulnerabilities.
Actionable Tips:
Configure Swagger UI or a similar tool for automated scanning and documentation of your network's APIs. Here's a basic example of how to set up a Swagger configuration file (swagger-config.yaml) for API documentation:
swagger: '2.0'info: title: Sample API description: API documentation for our sample API version: 1.0.0host: api.sample.combasePath: /v1schemes: - httpspaths: /users: get: summary: Gets a list of users responses: 200: description: Successful responseImplement automated tools like Apigee or Kong to get detailed analytics and security insights for your APIs.
Use Postman to manually test endpoints.
Use Check Point’s endpoint security solutions for comprehensive zero-day protection.
2. Explore API Marketplaces
API marketplaces provide a platform for discovering and using APIs and offer community feedback, security insights, and usage analytics. They are ideal for finding APIs vetted and reviewed by other developers and companies.
Actionable Tips:
Use platforms like Check Point API Reference to explore APIs that fit your automation needs.
Use APIs.guru for exploring well-documented OpenAPI files. For example, imagine you are interested in integrating a weather API. By searching for "weather" on APIs.guru, you find several options.
3. Conduct Regular API Audits
API auditing systematically reviews and analyzes APIs to ensure they are secure, efficient, and compliant with relevant standards and policies. In addition, regular audits can uncover performance issues and inefficiencies in API designs and help keep API documentation up to date.
Actionable Tips:
Implement tools like Burp Suite or OWASP ZAP for in-depth security scanning of your APIs.
# Automated scan using OWASP ZAPzap-cli startzap-cli open-url http://your-api-endpoint.com
zap-cli active-scan --recursive http://your-api-endpoint.com
zap-cli alerts -l InformationalUse automated scripts to regularly test your API endpoints against common vulnerabilities like SQL injection, cross-site scripting (XSS), etc.
import requestsfrom bs4 import BeautifulSoupExample of a simple script to test for XSS vulnerabilitydef test_xss(api_endpoint): payload = "<script>alert('XSS')</script>" response = requests.post(api_endpoint, data=payload) if payload in response.text: print(f"Potential XSS vulnerability detected in {api_endpoint}")test_xss("http://your-api-endpoint.com/api/v1/login")Regularly check APIs against industry standards like RESTful API guidelines.
4. Understand API Specifications
Deep knowledge of API specifications is key to understanding how APIs interact with your systems. This step involves thoroughly examining API documentation, focusing on authentication, authorization, and data handling practices.
Actionable Tips:
Use tools like Check Point’s AI-powered Infinity to prevent threats across your entire security infrastructure, including endpoints.
Use Redoc to generate user-friendly API documentation.
Define a routine for periodically reviewing and updating API specifications. For example, you can create an automation script with swagger-cli like this:
#!/bin/bash# Script to pull latest API specs and update documentationgit pull origin masterswagger-cli bundle -o ./path/to/swagger.yaml ./path/to/api-specs/echo "API specifications updated and bundled with Swagger."5. Implement API Gateways
API gateways are the entry point for managing and securing API traffic. They provide essential functions like authentication, rate limiting, request/response transformation, and collecting analytics.
Actionable Tips:
Configure security policies in Amazon API Gateway. For example, you can set a rate limit in the API Gateway throttling setting like the below:
{ "Type": "TOKEN_BUCKET", "rateLimit": 100, "burstLimit": 200 }Enable logging and monitoring in your API Gateway settings. For AWS, this can be done by integrating with CloudWatch. The below alarm configuration triggers an alert if there are more than 50 5XX errors within 5 minutes.
{ "AlarmName": "High API Traffic", "MetricName": "5XXError", "Namespace": "AWS/ApiGateway", "Statistic": "Sum", "Period": 300, "EvaluationPeriods": 1, "Threshold": 50, "ComparisonOperator": "GreaterThanThreshold"}6. Use open-appsec
open-appsec is one of the best web application firewall (WAF) and API security solutions. It stands out with its innovative ML-based engine that continuously learns and adapts to ensure your API security measures stay ahead of evolving cyber threats.
open-appsec is not limited to API security; it offers a variety of other benefits, too:
Prevents OWASP-10 and zero-day threats automatically with the ML engine.
Continuous monitoring ensures your web applications are always protected.
Easy integration with Kubernetes, NGINX, GraphQL, HELM, and more.
Automatically stops and blocks malicious requests.
Protects against over 2,800 Web CVEs based on award-winning NSS-Certified IPS.
Sets a cap on how many requests can be made to APIs within a certain period.
open-appsec is an open-source project that builds on machine learning to provide pre-emptive web app & API threat protection against OWASP-Top-10 and zero-day attacks. It simplifies maintenance as there is no threat signature upkeep and exception handling, like common in many WAF solutions.
To learn more about how open-appsec works, see this White Paper and the in-depth Video Tutorial. You can also experiment with deployment in the free Playground.