What is API Security? 8 Core Concepts and Examples
1. Authentication and Authorization
Authentication confirms user identity, while authorization controls what each user can access. OAuth 2.0 is the preferred API token-based access, allowing you to grant scoped access without exposing credentials. With tools like Auth0 and Okta, you can set up OAuth to limit access based on custom user roles or application needs, while libraries like passport.js (Node.js) and Spring Security (Java) support OAuth flows.
Consider integrating MFA with OpenID Connect (OIDC) on OAuth 2.0 to add an extra verification layer that protects sensitive endpoints even if an access token is stolen.
2. Input Validation
Input validation blocks malicious payloads, which can prevent injection attacks like SQL or XML injection. Use allowlist-based validation to define strict input formats for endpoints, allowing only approved data types, ranges, or characters. Allowlisting makes it harder for attackers to manipulate requests to bypass filers.
In Node.js, express-validator helps set up validation quickly, while OWASP’s ESAPI provides pre-built functions for secure input validation across different languages.
const { body } = require('express-validator'); app.post('/api/data',
[ body('username').isAlphanumeric().isLength({ min: 3, max: 15 }), body('email').isEmail() ],
(req, res) => { // Process validated data });3. JSON Web Tokens
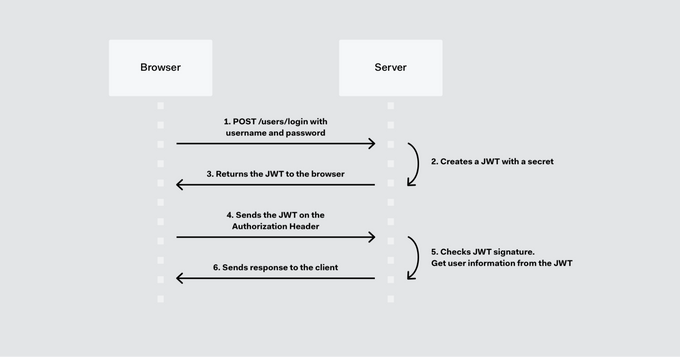
JSON Web Tokens (JWTs) simplify stateless authentication by storing user claims within the token, reducing database load and expediting user verification. However, JWT implementation must be cautious, especially in how tokens are handled and stored. Securely store your tokens in HTTP-only cookies or secure storage to avoid client-side tampering. For example, JSONwebtoken in Node.js is a popular library for JWT implementation.
Use short-lived tokens combined with refresh tokens to balance security and user experience. A 15-minute expiration works well to mitigate token hijacking:
const jwt = require('jsonwebtoken');
const token = jwt.sign({ userId: 123 }, 'secretKey', { expiresIn: '15m' });4. Rate Limiting
Rate limiting can help fend off brute-force and DDoS attacks. By capping the requests a client can make in a given timeframe, you keep traffic in check and prevent resource overload.
const rateLimit = require('express-rate-limit');
const limiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 100 // limit each IP to 100 requests per windowMs
});
app.use('/api/', limiter);5. Encryption
Without encryption, your data is open to interception and tampering. Transport Layer Security (TLS) safeguards data in transit, while field-level encryption protects specific sensitive details, like payment information, within API requests. Remember that keeping your encryption keys secure is as important as encrypting the data.
For APIs dealing with especially sensitive data – such as financial or health information – end-to-end encryption (E2EE) is recommended. E2EE encrypts data at the origin and keeps it encrypted to the final destination, so even if it passes through multiple services, only the sender and recipient can decrypt it.
6. API Gateways
API gateways act as centralized security checkpoints, allowing you to enforce uniform policies across all endpoints for authentication, rate limiting, and traffic inspection. They are particularly beneficial in microservices architectures to simplify security across dispersed services. Consider using gateways to segment your sensitive internal APIs from public ones. Kong Gateway and Apigee from Google are popular options.
7. API Security Testing
You must establish ongoing checks to catch new vulnerabilities as your APIs evolve and business needs and integrations change. Jit can facilitate these checks by leveraging OWASP Zed Attack Proxy (ZAP) for DAST testing to simulate real-world attack scenarios that might impact your APIs.
Jit’s scans actively probe for issues like SQL injection, cross-site scripting, and configuration flaws, giving you a clear view of your API’s defenses. You can set up daily scans or trigger tests with each deployment. Choose authenticated scans for deeper insight, or run quick, unauthenticated scans to spot surface security misconfigurations.
8. Cross-Origin Resource Sharing (CORS)
CORS configuration controls how domains interact with your API, protecting against cross-origin attacks. CORS policies allow you to specify which external origins can access resources, preventing unauthorized domains from exploiting data or functionality. Misconfigurations in CORS settings can lead to data leakage, so adopting a default-deny stance is critical, only allowing trusted origins to access your API.
const cors = require('cors');
app.use(cors({
origin: 'https://trusted-origin.com',
methods: 'GET,POST'
}));Establish Resilient API Security with Jit
APIs are powerful assets—but only if you manage their risks so the benefits outweigh the vulnerabilities. Each API is a direct line into your data and services, making them attractive targets for malicious actors. The key here is implementing proactive, built-in security measures to keep your APIs secure without impacting your development speed.
Jit’s ASPM platform brings an automated layer to API security, conducting real-time security assessments at every code change and catching vulnerabilities before deployment. Jit’s edge lies in prioritizing high-risk issues, guiding teams with automated remediation paths that keep development fast and focused. Explore it today.